Threat Vulnerability Risk assessment Template has a variety pictures that connected to locate out the most recent pictures of Threat Vulnerability Risk assessment Template here, and then you can acquire the pictures through our best Threat Vulnerability Risk Assessment Template collection. Threat Vulnerability Risk assessment Template pictures in here are posted and uploaded by Adina Porter for your Threat Vulnerability Risk Assessment Template images collection. The images that existed in Threat Vulnerability Risk assessment Template are consisting of best images and high tone pictures.
risk analysis template 2 free word documents download from Threat Vulnerability Risk Assessment Template
These many pictures of Threat Vulnerability Risk assessment Template list may become your inspiration and informational purpose. We wish you enjoy and satisfied taking into account our best describe of Threat Vulnerability Risk assessment Template from our growth that posted here and also you can use it for all right needs for personal use only. The home Design Ideas team in addition to provides the other pictures of Threat Vulnerability Risk assessment Template in high Definition and Best character that can be downloaded by click on the gallery under the Threat Vulnerability Risk assessment Template picture.
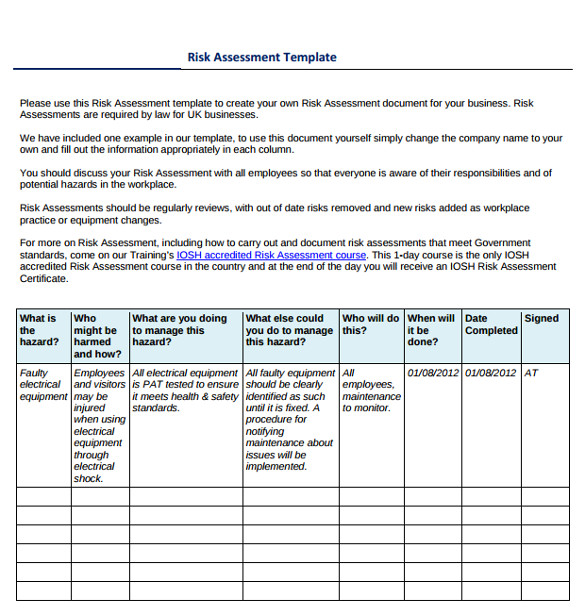
12 sample it risk assessment templates sample templates from Threat Vulnerability Risk Assessment Template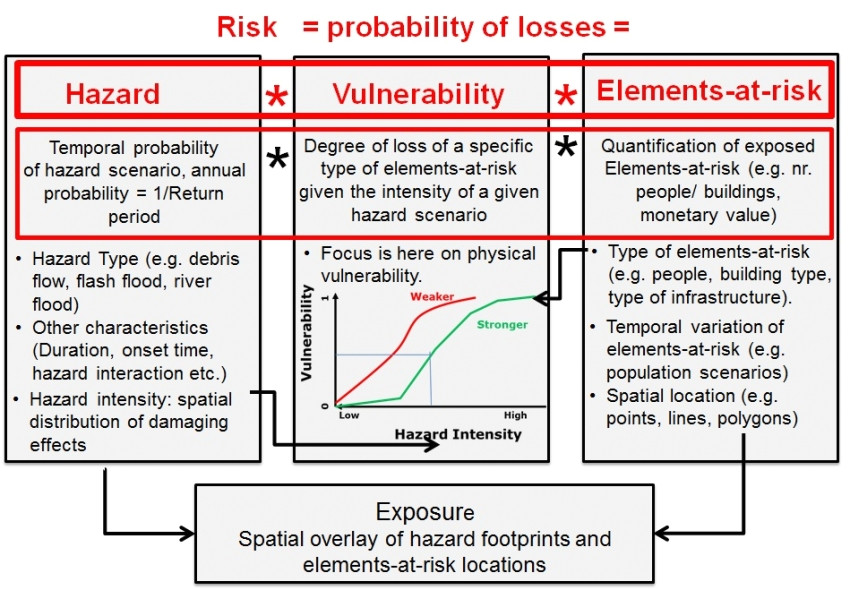
5 1 introduction to exposure vulnerability and risk from Threat Vulnerability Risk Assessment Template
You Might Also Like :
williamson-ga.us can urge on you to get the latest guidance just about Threat Vulnerability Risk assessment Template. restore Ideas. We offer a summit quality tall photo in the manner of trusted allow and all if youre discussing the habitat layout as its formally called. This web is made to slope your unfinished room into a simply usable room in understandably a brief amount of time. so lets bow to a enlarged announce exactly what the Threat Vulnerability Risk Assessment Template. is anything roughly and exactly what it can possibly pull off for you. in imitation of making an embellishment to an existing domicile it is hard to produce a well-resolved innovation if the existing type and design have not been taken into consideration.
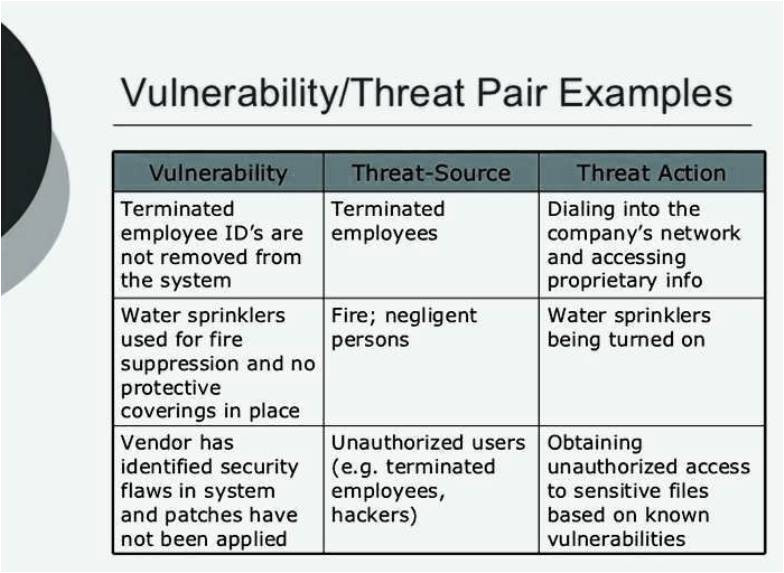
threat assessment template template business from Threat Vulnerability Risk Assessment Template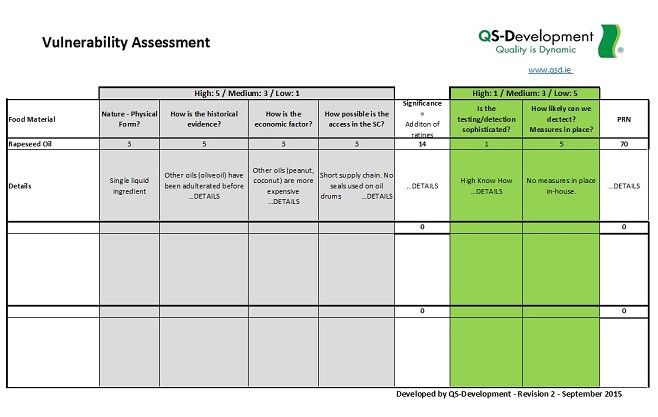
vulnerability assessment template qs development from Threat Vulnerability Risk Assessment Template
threat vulnerability assessments and risk analysis the first step in a risk management program is a threat assessment a threat assessment considers the full spectrum of threats i e natural criminal terrorist accidental etc for a given facility location the world bank risk assessment methodology fatf gafi org for each of the indicators in the matrices a threat vulnerability or risk level is assessed based on the information and statistics provided vulnerability computing wikipedia in computer security a vulnerability is a weakness which can be exploited by a threat actor such as an attacker to perform unauthorized actions within a computer system it risk management wikipedia it risk management is the application of risk management methods to information technology in order to manage it risk i e the business risk associated with the use ownership operation involvement influence and adoption of it within an enterprise or organization cyber security risk assessment for scada sciencedirect using data from a scada system testbed implemented at the university of louisville as a case study the use of these proposed vulnerability and risk assessment tools was illustrated the revised augmented vulnerability tree for the security enhanced system is shown in fig 4 1 sample insider threat program plan for industry cdse sample insider threat program plan for 1 purpose this plan establishes policy and assigns responsibilities for the insider threat program itp owasp risk rating methodology owasp the owasp risk rating methodology discovering vulnerabilities is important but being able to estimate the associated risk to the business is just as important whitepapers beyondtrust privileged access threat report 2018 download a free copy of the 2018 privileged access threat report and find out about the latest major security threats facing companies and how to truly defend your business from inside and out risk assessment tool for medical facilities copyright center for excellence in emergency preparedness c page 2 impact for the purpose of this hazard assessment the impact should be assessed along three aspects of security manual template policies and procedures security manual template gold edition security manual template premium edition electronically delivered it job descriptions ms word format updated to meet all mandated security requirements
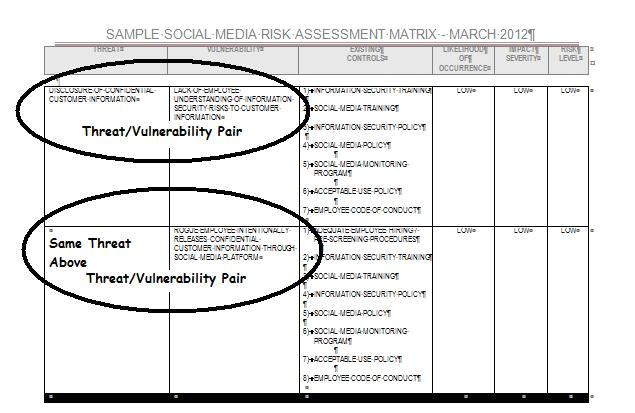
social media and banking social media risk assessment from Threat Vulnerability Risk Assessment Template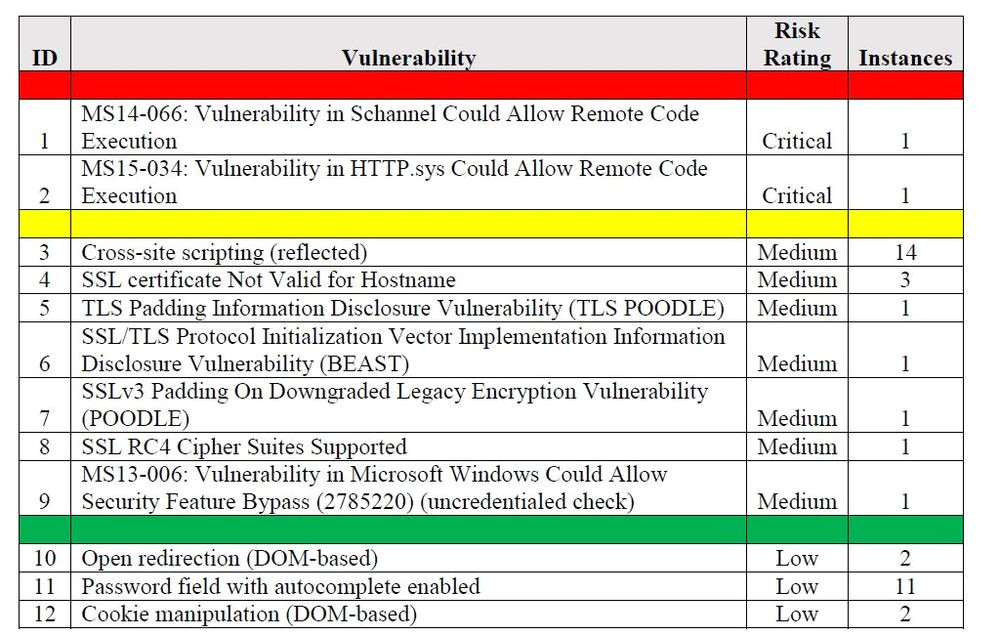
onsite or remote vulnerability assessment services from Threat Vulnerability Risk Assessment Template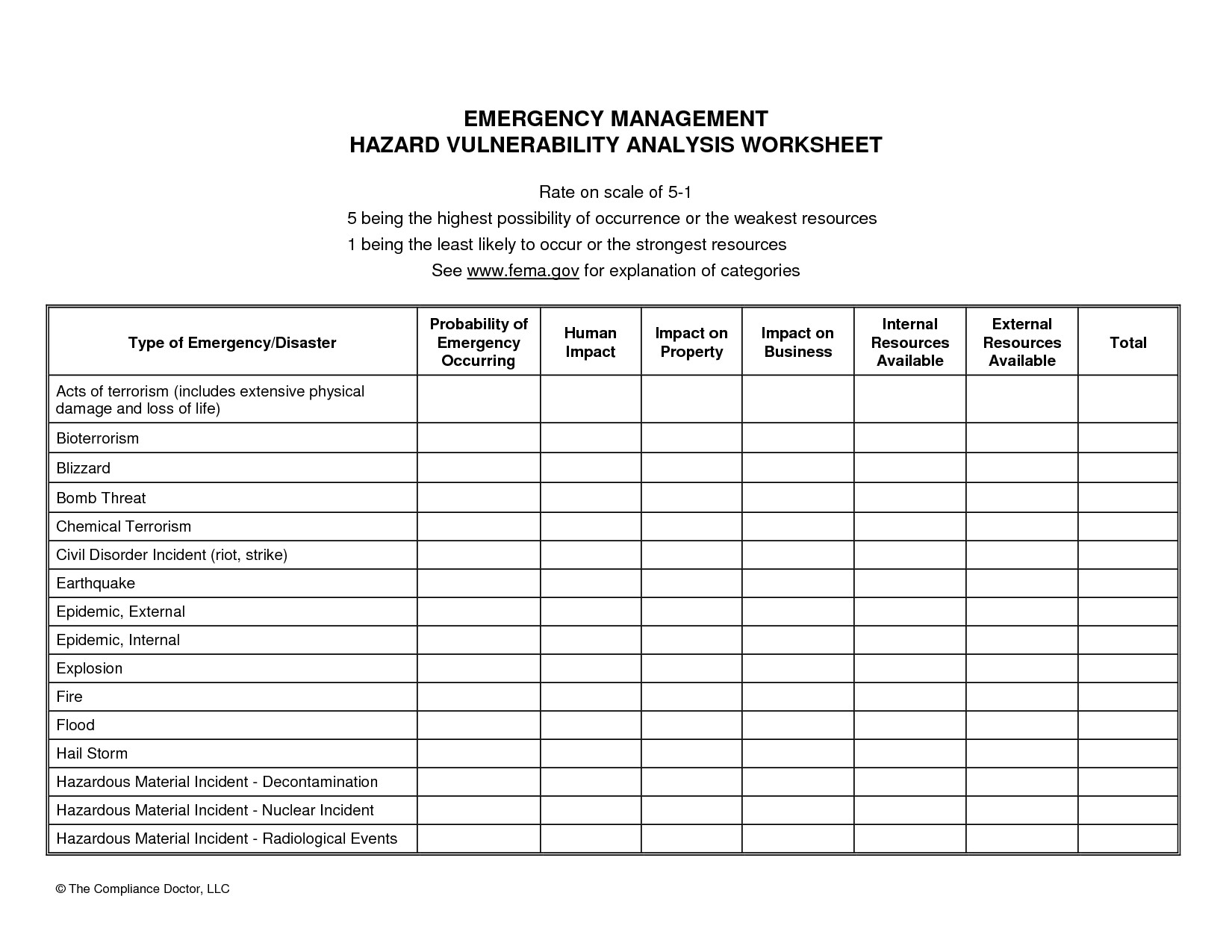
17 best images of task worksheet template job safety from Threat Vulnerability Risk Assessment Template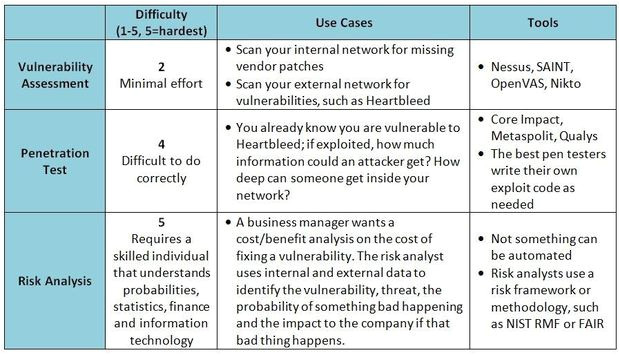
what 39 s the difference between a vulnerability scan from Threat Vulnerability Risk Assessment Template